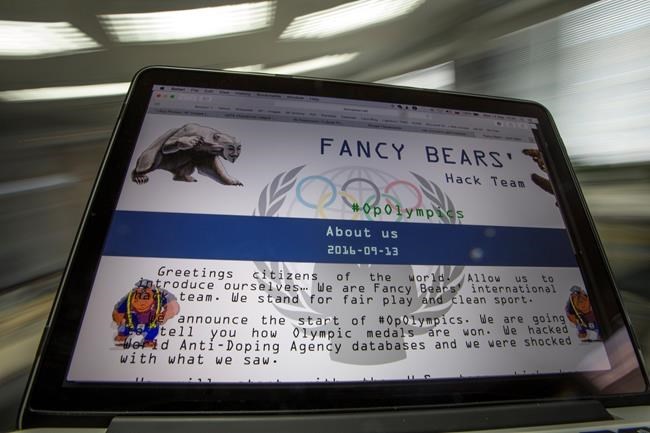
FILE - This Wednesday, Sept. 14, 2016, file screenshot shows the Fancy Bears website fancybear.net on a computer screen in Moscow, Russia. Having made their name by breaching a World Anti-Doping Agency database, the so-called “Fancy Bears” hackers appear to be changing tack by seeking to peddle stolen emails directly to the media. Out of the blue and unsolicited, they contacted an Associated Press journalist with a dump of hundreds of emails seemingly stolen from the Canadian and U.S. anti-doping agencies. (AP Photo/Alexander Zemlianichenko, File)
December 24, 2016 - 5:26 AM
PARIS - The message dropped unsolicited into my private Twitter inbox.
"Hello, we are Fancy Bears' Hack Team," said the message, illustrated with an image of a sharp-clawed bear wearing a mask. "Are you interested in WADA and USADA confidential documents?"
More than 200 emails apparently stolen from employees at the United States and Canadian agencies that police doping in sports then followed to me and The Associated Press, with another message: "Let us know if you find the material newsworthy."
Coming after investigative reports that detailed the depth of unprecedented state-sponsored Russian doping operations , the motive seemed clear: to prove that drug cheats and deception aren't exclusive to Russia. The hackers are perhaps related — or perhaps not — to electronic thieves now accused by U.S. security agencies of meddling in the presidential election to help Donald Trump win. They gave away little in their exchanges that would reveal their identity.
As it turned out, the emails were less newsworthy than the way the Fancy Bears tried to peddle them. The strategy of approaching a journalist directly would represent a shift for the mysterious hacking group, which previously ignored journalists' messages.
The Bears made headlines in September when they claimed credit for breaching a World Anti-Doping Agency database and publishing documents on the web that detailed athletes' medical exemptions to use drugs otherwise banned in sports.
WADA, citing law enforcement authorities, said those behind the breach were Russians seeking to retaliate for the embarrassing revelations of Russian doping coverups on an industrial scale.
Analysts immediately wondered if the Bears were part of a stable of shadowy groups — including the WikiLeaks knockoff DCLeaks and purported Democratic National Committee hacker Guccifer 2.0 — which U.S. intelligence have tied to Moscow . The name Fancy Bears was provocative: it's nearly identical to the code name researchers at threat intelligence company CrowdStrike use for the group accused of being behind the DNC hack and a host of other high-profile attacks dating back to 2008 or earlier. This Russian-linked group of hackers is also known to experts by an array of other monikers, including APT28, Tsar Team or Strontium.
Some researchers have found overlap between the Bears and other Kremlin-linked groups, but hard evidence is often hard to come by in hacking cases and there are some signs that the group littered its electronic trail with red herrings. The group that contacted me gave few additional clues.
When I asked why they adopted the name Fancy Bears, they wrote back: "You like it?"
When the hackers uploaded sheaves of documents from the WADA database in September, they declared: "We'll keep on telling the world about doping in elite sports. Stay tuned for new leaks."
They seem to be making good on the promise. Some of the stolen emails sent to me — apparently sent and received by the Canadian Centre for Ethics in Sport, which manages anti-doping in Canada — were dated as recently as mid-October, suggesting the Bears continued to hack anti-doping computer systems months after their first intrusion.
Their original leaks caused a splash.
Tour de France winner Bradley Wiggins, most notably, faced uncomfortable questions after the stolen material showed he had medically approved corticosteroid injections. The Briton said the shots were to prevent hay fever.
Simone Biles confirmed she has attention-deficit disorder after leaked medical waivers showed the Olympic champion gymnast has long had permission from her sport's governing body to take daily pills for the condition.
But lately interest has waned. Rather than proving doping, the dump over two weeks of more than 200 waivers in September merely demonstrated that sports have a functioning, mutually agreed-upon system — however imperfect at times — that allows athletes with recognized medical conditions to take drugs without falling foul of anti-doping regulations.
WADA's subsequent assertions that 18 of the Bears' leaked waivers were, in fact, fabricated also dented the hackers' credibility. Most of all, the significance of the leaks paled in the face of mounting proof of hard-core Russian doping — a crisis more dangerous for sports than whether some athletes are seeking waivers for treatments they don't really need.
In contacting the AP directly, the Bears wrote in a private message: "By the way have you seen the latest leak on our website? What do you think about it?"
In another message offering me stolen documents, the Bears said they had documents involving a prominent Western Olympian and information about Ultimate Fighting Championship participants and the fat-burning drug clenbuterol. None of the subsequent emails identified doping violations.
The messages to AP appear to be part of Fancy Bears' first foray into media outreach. Around the same time as they were talking to me, a group claiming to be the Bears also reached out to Andy Brown of the Sports Integrity Initiative with an identical pitch, according to an account of the exchange published Thursday.
"They're crafting the way that they leak in a much smarter way," Matt Tait, a British cybersecurity expert who is investigating the group.
Fancy Bears may be new to the game, but DCLeaks and Guccifer 2.0 have exhibited similar behaviour — first making a splash with newsworthy leaks on purpose-built websites and then following with more discreet attempts to reach journalists individually and market niche material.
Guccifer 2.0 contacted another AP journalist in August to offer information about Democratic Party operations in Pennsylvania. The AP did not discover anything immediately newsworthy in the dump and eventually Guccifer 2.0 published the material to its own site.
The Bears denied they were trying to squeeze extra mileage out of their material by getting me involved.
"We are pretty satisfied with media coverage," they said. "We have too many documents so there's a possibility we could miss some really interesting stuff. Thus, we just would like to know professional opinion on these documents."
___
Jack Gillum in Washington and Raphael Satter in Paris contributed.
News from © The Associated Press, 2016